Vendors must do better when it comes to vulnerability disclosure
Now in its third year, IoTSF’s latest research report on Consumer Vulnerability Disclosure continues to shine a light on the poor performance of industry on the basic practice of vulnerability disclosure. Whilst incremental gains have been made, they are small and not worthy of celebration.
- In 2018, a mere 9.7% of the study cohort had a detectable disclosure policy.
- In 2019, that number increased – slightly – to 13.3%.
- In 2020, the period covering this report, there’s a small increase again to just 16.3% (18.9% when adjusted – see below.)
This fails to impress on two fronts:
- This is a basic security hygiene practice and IoTSF believes that consumers deserve better – we’d like to see that number close to 100%, ideally 100%!
- The rate of adoption is glacial and does not match the pace at which new products are entering the market.
In this report, we have expanded the view to include more categories – hence the 18.9% figure which gets a boost from more traditional and mature product categories such as WiFi and Networking. Yet newer categories such as ‘smart home’ do not fare nearly so well. The extra categories have been added to track market developments and build out a harmonised set of categories consistent with market analyst studies and reflecting areas most likely to be included in future legislation.
For this study, products have been grouped into appliances, audio, childcare, energy, environment control, garden, health fitness and wellbeing, hub, laptops, PCs and tablets, leisure & hobbies, lighting, maintenance, mobile, pet care, safety, security, smart home, toys, TV, wearables, Wi-Fi and networking and workplace.
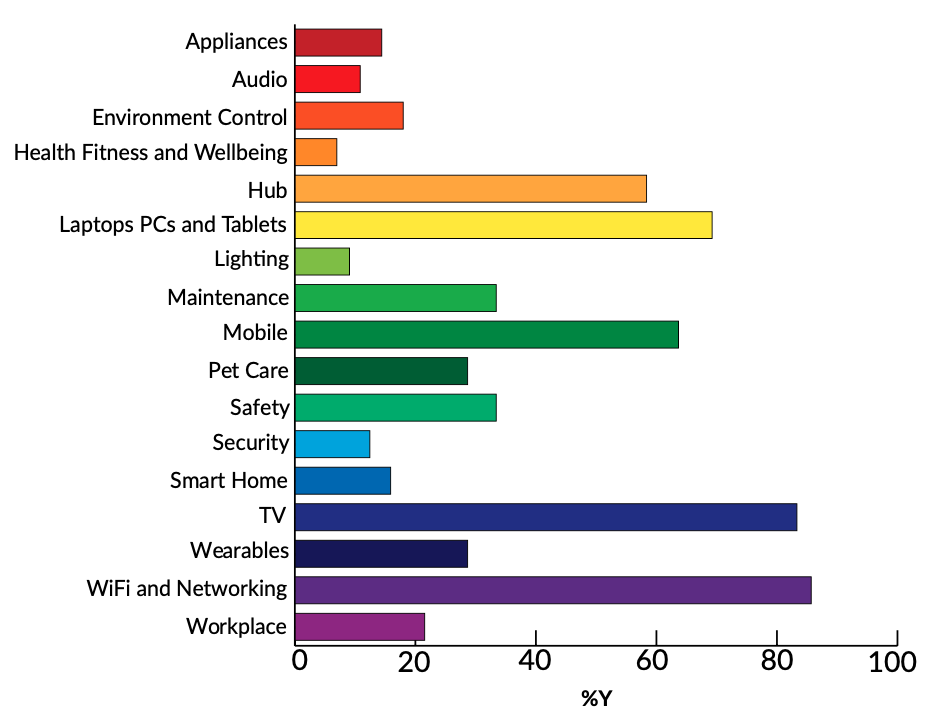
The report also contains data on regional variations as in prior years and in addition, we consider how many of the companies that do have a disclosure policy would likely be compliant with the proposed wording of UK legislation. We have applied a filter – or threshold test – to show a basic and extended handling of disclosures. Whilst 64 companies qualified for the basic threshold, only 4 companies qualified for the extended threshold in our study. These companies are details in the report.
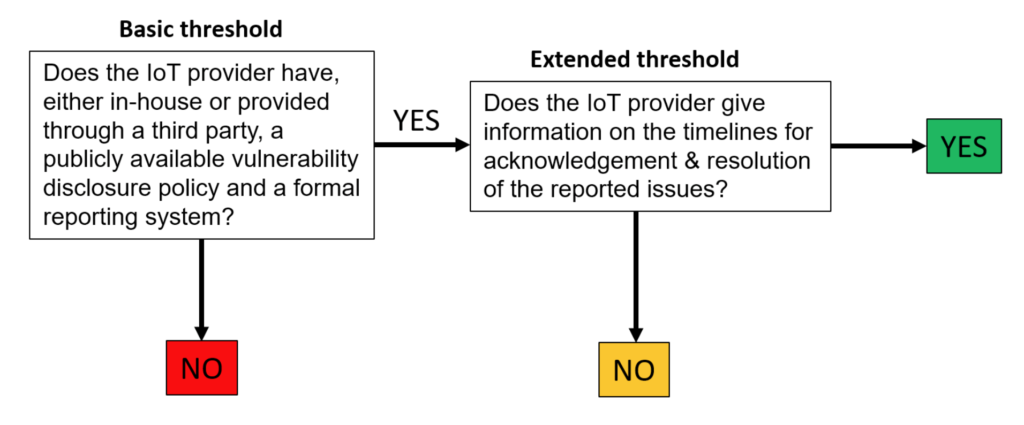
The report concludes that the responsibility of IoT manufacturers to their customers is clear, but also that they don’t have to tackle security issues alone. Vulnerability disclosure brings the wider security research community to the table, joining forces in the mission to build and maintain IoT products that consumers can trust.
The 47-page report can be downloaded for free from the IoTSF website and includes the study data in 6 appendices.
Click cover or click here to download the report






