As a new member of the IoT Security Foundation, we asked the CEO of Crypto Quantique, Dr Shahram Mossayebi, to tell us how they are offering silicon vendors a unique hardware IP solution and complementary software platform to solve a number of security challenges including scalability, identity and cost.
An economical approach to creating unforgeable identities and secure connectivity in IoT systems.
Dr Shahram Mossayebi, CEO, Crypto Quantique
Connectivity and the IoT are at the heart of so many things in today’s world and the number of connected devices is growing massively. There are many reports of billions of IoT devices being around already and, looking at the big picture, a central question is how you can manage all these connected devices that are integrated into our lives, and how can you reliably identify them in the field. That brings up the question of device identities.
The identification challenge
Like humans that have different identities and personas in the real world, in the digital world, the same concept applies to devices. For example, your mobile phone is a digital device that you can use to identify yourself, but the device also has to identify itself to access various services.
So, there’s the concept of a digital identity for the device on its own. This is playing a central role in the future of IoT connectivity, and not just in consumer electronics but in industrial IoT applications too.
If you want to exploit the potential of connected devices or the IoT, you need end-to-end security. You need to be able to make sure you can access devices in the field remotely while being certain that you’re talking to the right device. Then the device must identify you as the authorized entity to send those commands. Only then should it execute the commands, otherwise it must ignore them. Unless you have a unique and unforgeable identity for each device, you cannot build a secure system.
There’s growing agreement that the identity of the device has to be part of the fabric of the hardware. Software can be circumvented by software, so you need something that’s hard-coded. It’s like the DNA inside the device that nobody can change. Exploiting a quantum phenomenon, quantum tunneling inside the devices, is one approach that gives you a fingerprint that is unforgeable, that is unique, that is random inside the device, and that nobody can predict. If you can also generate cryptographic keys from that source, and other secure credentials inside the device over its entire life cycle, you have a strong root-of-trust, or RoT.
How you can reduce costs while increasing IoT security
The cost of security is always an issue for customers but if you can work with standard CMOS processes to integrate the RoT inside a microcontroller or ASIC so that it’s fabricated as part of that design, it’s much more economical that having to change or add to these processes.
A number of IoT security approaches exploit PUFs – Physical Unclonable Functions – to generate random strings through hardware variability. We exploit quantum tunneling through the nano-structure variation of the CMOS technology to generate randomness and we generate randomness not just one string but many of them, within the main component, so it’s secure. This approach is also inherently secure against side-channel attacks, which is another significant benefit.
On demand, we generate multiple, uncorrelated cryptographic keys internally, inside the device. No key storage is needed. Some of these keys can be used to generate identities. Others can be used for symmetric or asymmetric cryptography, and others for authentication. Because you have that capability internally, you don’t need to rely on other auxiliary key management solutions on the hardware side, any of which will add substantial cost and introduce risk.
Solving the hardware software disconnect
Another challenge we saw in the IoT ecosystem was a disconnect between hardware security and software security. There are various hardware security options in the market, but it’s a huge task for companies to be able to take advantage of them. Some can take a month to get up and running – it’s complicated embedded technology. We approached this by developing a software platform in which everything needed for the end-user to take advantage of hardware security inside the device is accessible in one tool. It helps them with all three stages of device deployment within an IoT network – provisioning, onboarding, and lifecycle management. So once end-users have suitable hardware IP inside their devices, they can handle secure provisioning in a third-party programming house without the involvement of that programming house becoming any kind of security risk.
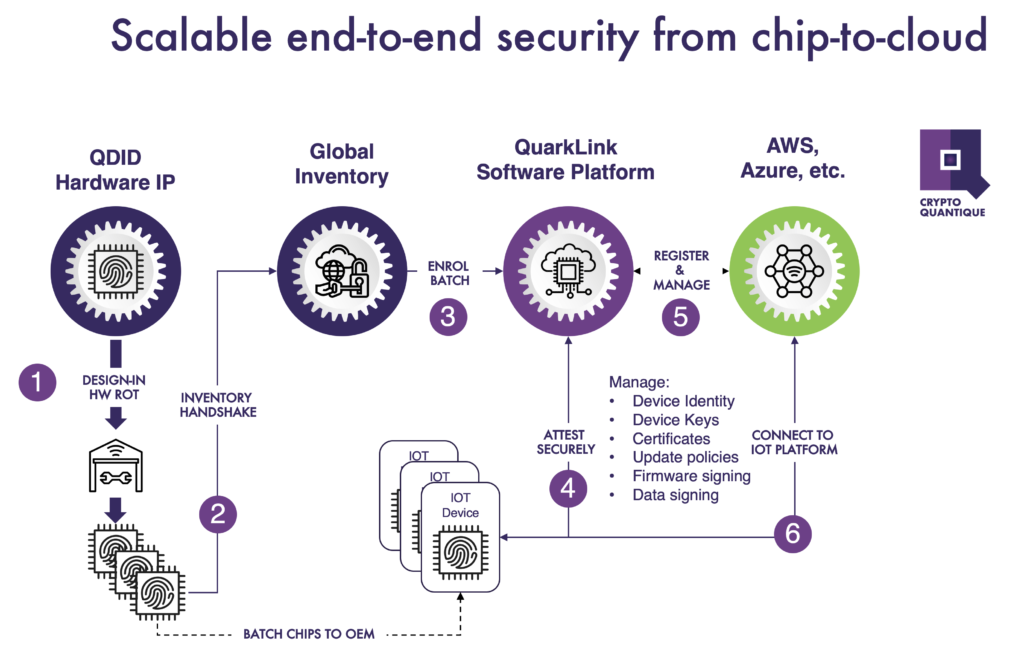
The tool enables onboarding to multiple IoT platforms, handling enrollment and registration to those platforms. After that, it helps monitor the certificates, the keys, the identities of the devices, and manages them easily if users want to renew some, revoke some, generate new ones, et cetera. With a couple of clicks, end users can achieve security without really knowing much about cryptography or the various industry standards. They have full control and can run the tool on any infrastructure that they have, whether it’s on-premises or on private or public clouds. They own their security, from the software point of view, including the source code. Nobody has access to their secrets and none of the secrets of the devices are known to anyone else due of the way keys are being generated inside the device. Customers have a tightly controlled, closed security system in their own hands.






