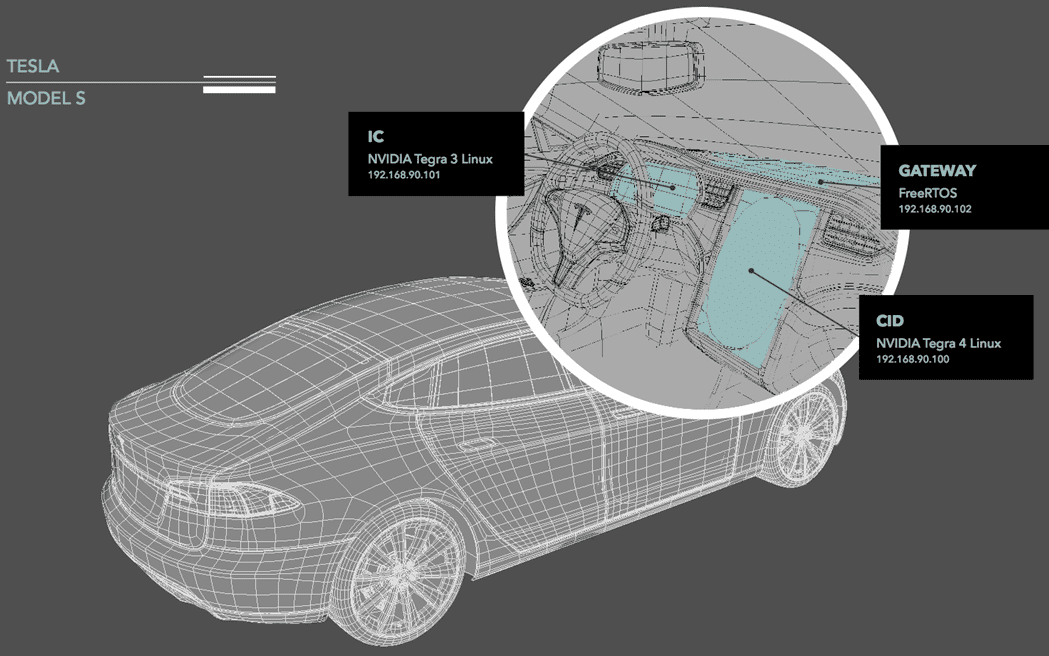
In his talk “What I learned about IoT from hacking the Tesla Model S” given at the IoT Security Foundation’s inaugural conference (Royal Society, London, Dec ’15), Marc Rogers outlined how he managed to hack into the electronic systems of the iconic $90,000 car.
Yet despite finding a number of significant vulnerabilities, Marc not only thinks the Tesla is robust, he goes much further and says:
“We believe that the Tesla Model S is an archetype for what all cars will look like in the future – others will follow”
Marc and his white hat associates were not expecting to be impressed, but they found it was much harder to compromise the Tesla than they expected. It took a “hacker Olympics”, taking place over 3 months to identify 6 vulnerabilities in which they used a variety of methods in their attempts to compromise the hardware, wireless, network, browser, linux, binary (and more) systems.
On the plus side, this “data centre on wheels” has been well architected yet the suspected short cuts in the production process meant that the Tesla was left exposed in places where it should not have been. Was encryption used? Were VPN keys stored on removable media? Surely default or plain text passwords were not used? You might be surprised.
Despite what was achieved, Tesla’s reputation emerge’s not only intact, but enhanced from the experience. Marc was impressed by the response he received, Tesla not only listened, their CTO presented him with a token of their appreciation and they got to work pretty quickly to fix the problems.
Having hacked the Tesla, Marc reflected on what this means for the automotive industry where modern tech (and its accompanying software) is disrupting traditional thinking.
IoTSF would like to thank Marc for sharing his insight and thoughts with us (and let us know when you’ve acquired a Faraday Future to play with).
You can watch the full talk here.

Marc Rogers
Head of InfoSec at Cloudflare Inc.






