Whilst it is true that good digital security is derived from sound and fundamental principles, it is also true that context is all – no solution exists that satisfies all requirements across all applications. If that were not the case, security (or insecurity) would not be on the top 3 list of issues for IoT today. This is true for the application, business, operating and technical domains hence, where solutions are being offered, it is crucial to marry domain experience with security expertise.
As IoTSF builds out its strategy of making it safe to connect, it recognizes the need to reach further into application domains and unite professional communities. This helps to ensure fit-for-purpose defenses are co-created by both sets of practitioner but also has the benefit of aiding adoption as collaboration and consensus building tends to reduce friction. We invited Alan Mihalic, from Norman Disney & Young, to give us an IoT security perspective from the global construction industry. It’s a familiar story; IoT represents a very real opportunity for the sector, but the threats and the risks have to be carefully managed.

Over the decades, there have been a number of seismic shifts in technology; mainframe computing, client server, and cloud computing easily comes to mind. However, the most all encompassing with the inherent potential to change society as we know it has to be The Internet of Things – a seismic technology shift that will not only change the world as we know it, but perhaps more importantly, how we experience it. IoT will be at the core of the smart cities we live in, the smart buildings we occupy, even in the smart bodies we inhabit.
While fundamentally changing how build environments are designed and operated, this shift will expose buildings and all those associated with them to the increased likelihood of cyber attacks.
Industry forecasts the IoT market will grow from an installed base of 15.4 billion devices in 2015 to 30.7 billion devices in 2020 and 75.4 billion in 2025. Many of these devices will be deployed in buildings, public works and critical infrastructure. These smart technologies will establish an urban landscape that is all connected, all sharing, all knowing and imbued with functionality that can provide unprecedented levels of comfort and convenience. The convergence of Smart Technologies and the built environment will improve the operation and capabilities of buildings, but will also lead to increased vulnerabilities and attack vectors not previously encountered within design engineering and urban planning. Research suggests the impact on the building and construction industry will be significant. No longer are we looking at cyber attacks targeting at the company or user level; we now have attack vectors that can potentially shutdown a shopping precinct, a power grid, a major city, perhaps even a nation.
Anatomy of a Virus
Austrian Hotel – Shutdown and Locked Out
 One of the top European hotels, Romanantik Seehotel Jaegerwirt in Austria, became the target of cyber criminals. They managed to hack into the luxurious 4-star hotel’s electronic key system, rendering it useless. While the hotel guests were unable to move in and out of their hotel rooms, the cyber attackers demanded a ransom of over EUR 1500 in Bitcoin from hotel management. The security breach also managed to compromise the hotel’s reservation and cash desk systems, bringing the entire operation to a halt. Justifying the Hotel’s decision to pay the ransom, the managing director stated, “The hotel was totally booked with 180 guests. We had no other choice. Neither Police nor Insurance companies can help you in these circumstances.”
One of the top European hotels, Romanantik Seehotel Jaegerwirt in Austria, became the target of cyber criminals. They managed to hack into the luxurious 4-star hotel’s electronic key system, rendering it useless. While the hotel guests were unable to move in and out of their hotel rooms, the cyber attackers demanded a ransom of over EUR 1500 in Bitcoin from hotel management. The security breach also managed to compromise the hotel’s reservation and cash desk systems, bringing the entire operation to a halt. Justifying the Hotel’s decision to pay the ransom, the managing director stated, “The hotel was totally booked with 180 guests. We had no other choice. Neither Police nor Insurance companies can help you in these circumstances.”
In another major attack, Global hotel chain InterContinental Hotels Group Plc said 1,200 of its franchised hotels in the United States, including Holiday Inn and Crowne Plaza, were victims of a three-month cyber attack that sought to steal customer payment card data.
“The breach lasted from September 29 to December 29, InterContinental spokesman Neil Hirsch said on Wednesday. He declined to say if losses were covered by insurance or what financial impact the hacking might have on the hotels that were compromised, which also included Hotel Indigo, Candlewood Suites and Staybridge Suites properties.” SOURCE: BUSINESS INSIDER
These attacks can no longer be considered rare occurrences. The ability for cybercriminals to monetise their efforts has seen an increase in attacks directed at hospitals, universities, private businesses and even law enforcement infrastructure.
 Cybercriminals are focusing on building design and operational functionality to develop new attack vectors. A collision of building connectivity can allow an attacker access to Point of Sale systems via the HVAC network. The convergence of Information and Operational technology has seen the once isolated environment of “operational technology” connected to the IP network. This by default connects it to the Internet. Building management systems are now a conduit to an array of interconnected building and business services. A cyber attack that illustrates these emerging cyberattack vectors is the Target attack of 2013. Target POS systems were compromised by a computer from Target’s HVAC vendor. The stolen credentials of the HVAC vendor enabled access to Target’s application dedicated to vendors. Through a series of hacking activities the breach resulted in 40 million shopper credit and debit cards being compromised.
Cybercriminals are focusing on building design and operational functionality to develop new attack vectors. A collision of building connectivity can allow an attacker access to Point of Sale systems via the HVAC network. The convergence of Information and Operational technology has seen the once isolated environment of “operational technology” connected to the IP network. This by default connects it to the Internet. Building management systems are now a conduit to an array of interconnected building and business services. A cyber attack that illustrates these emerging cyberattack vectors is the Target attack of 2013. Target POS systems were compromised by a computer from Target’s HVAC vendor. The stolen credentials of the HVAC vendor enabled access to Target’s application dedicated to vendors. Through a series of hacking activities the breach resulted in 40 million shopper credit and debit cards being compromised.
Cyber Security by Design – Integrating building design and engineering into the development process
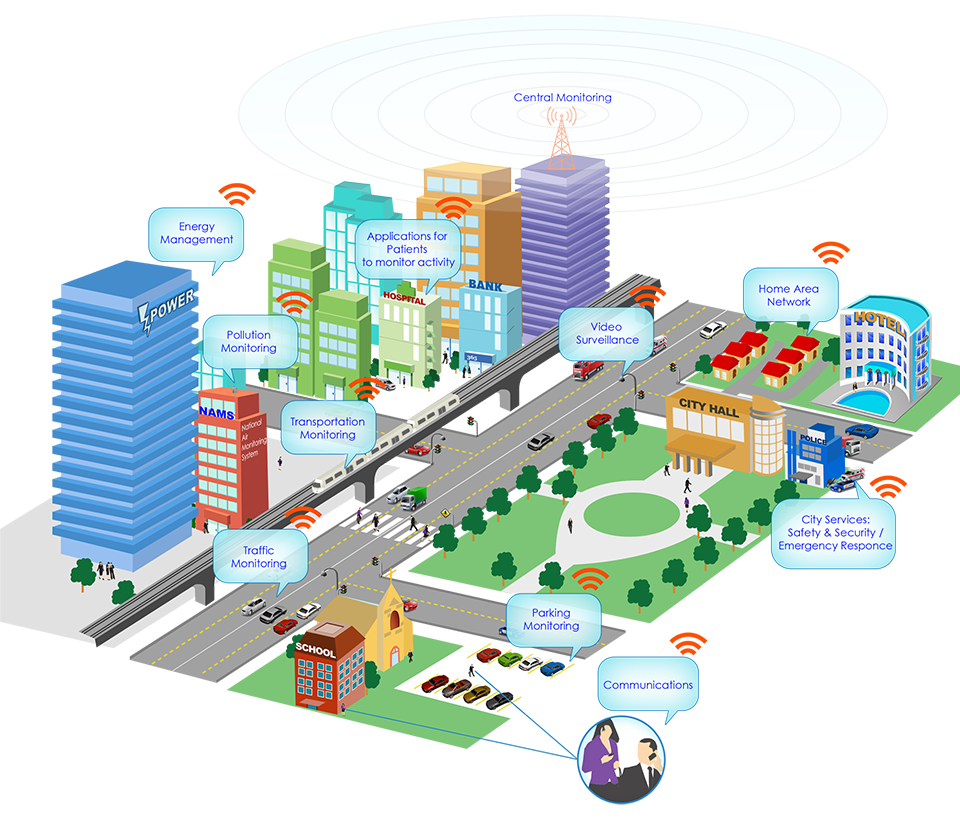
In an IoT world where a vending machine or Business Management System can potentially launch a cyber attack and disable your building’s critical services there is an imperative to address these likelihoods at all levels of the build design and deployment stages.
Builders, engineers and critical services specialists that do not factor in potential cyber risk threats as part of their design considerations expose their assets, their occupants and the public to unnecessary risk. The inclusion of smart technologies within building services and design considerations requires a collaborative approach to ensure security and privacy standards are maintained. This collaboration must extend to electrical and mechanical engineers, HVAC, fire safety, BMS, and audio visual specialists. Some within the building industry may consider this collaboration unnecessary, overly cautious, possibly even an attempt at scare mongering. However, this is far from the case. Building industry clients are increasing becoming aware how their brand is exposed in an all connected, always on digital age. They are looking at build environments as critical “defence points” to their overall service offerings and strategic objectives.
Increasingly, they are looking at designers and engineers to factor these concerns into their service offerings and solution submissions.
In a Smart Building all points of entry are possible Cyber Attack vectors
 Consider a corporate audio/visual refit. Company A (retail chain) requires a state of the art AV solution to enable its executive team to communicate in a timely and efficient manner.
Consider a corporate audio/visual refit. Company A (retail chain) requires a state of the art AV solution to enable its executive team to communicate in a timely and efficient manner.
An AV consultancy is engaged to provide a global solution that meets corporate requirements. They provide the design and outsource the implementation to a contractor. Functionality is confirmed according to design specifications and the project is considered completed. No design considerations have assessed data confidentiality, integrity or availability. In traditional terms, the system works, the job is done. At some point an executive meeting discussing global strategy and direction is scheduled. The AV solution works as expected. However, unknown to the participants the session has been hacked and confidential information is now a source of embarrassment and potentially ransom. The initial design did not consider how the solution equipment connected to its manufacturer, its reliance on converged network services or its obligation to corporate security policies and standards. This generic example can be extended out to traffic systems, hospital equipment, and government services. At its core is the ability to provide functionality whilst maintaining data confidential and privacy requirements. To consider these control requirements as information technology issues to be addressed by the organisation’s IT department is short-sighted and ultimately perilous. Cyber security is not an IT issue. In a digital smart age cyber safety is a design issue. It is reasonable to expect within the near future cyber security building services will require regulatory sign off not unlike fire and building safety. The stakes are too high. If an elevator system or shopping centre alarm system can potentially be disabled over an internet connection this becomes a safely issue. A public safety issue with serious public and private ramifications.
The news is not all bad. Collaboration and engagement is the key
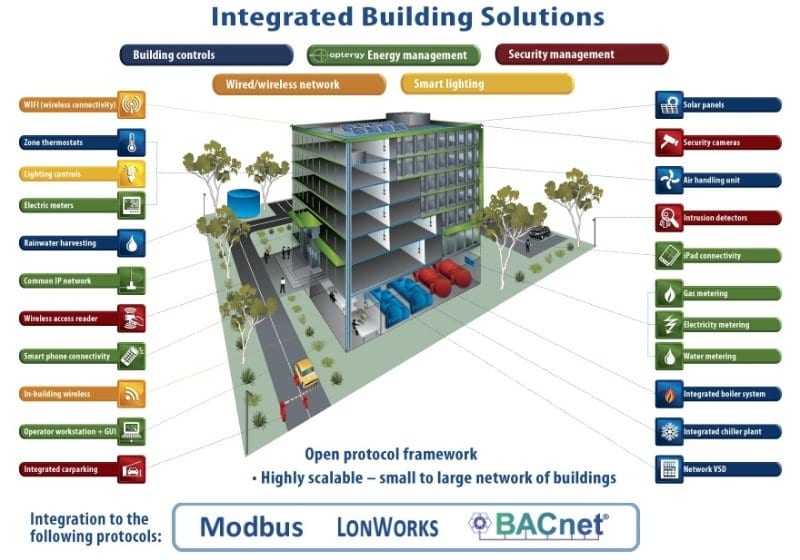 At the risk of having presented a dooms day scenario which is beyond salvation I would like to add the news is not all bad. Key to meeting these smart building cyber challenges is a willingness for key players within the building and construction industry to consider the cyber security issues that will inevitably impact upon their design decisions and solution offerings.
At the risk of having presented a dooms day scenario which is beyond salvation I would like to add the news is not all bad. Key to meeting these smart building cyber challenges is a willingness for key players within the building and construction industry to consider the cyber security issues that will inevitably impact upon their design decisions and solution offerings.
The incorporation of cyber security design frameworks and risk based analysis tools for building services needs to become part of the building industry professional’s toolkit. This by no means requires an HVAC specialist or design engineer become a cyber security expert, but it does require the consideration of cyber security controls to be factored into their designs. The cyber security industry is establishing a presence within the building industry which reflects these cyber security design concerns and is a conduit for building cyber safe practices and risk based mitigation strategies. The future of smart urban planning will usher in an era of creativity, functionality and convenience resulting in unprecedented opportunities. Key to this successful building services evolution will be the assurance that, private, public and corporate cyber safety is maintained and protected to community expectations.
 by Alan Mihalic, CISSP, CISM, ISSMP, ISSAP
by Alan Mihalic, CISSP, CISM, ISSMP, ISSAP
Norman Disney & Young





